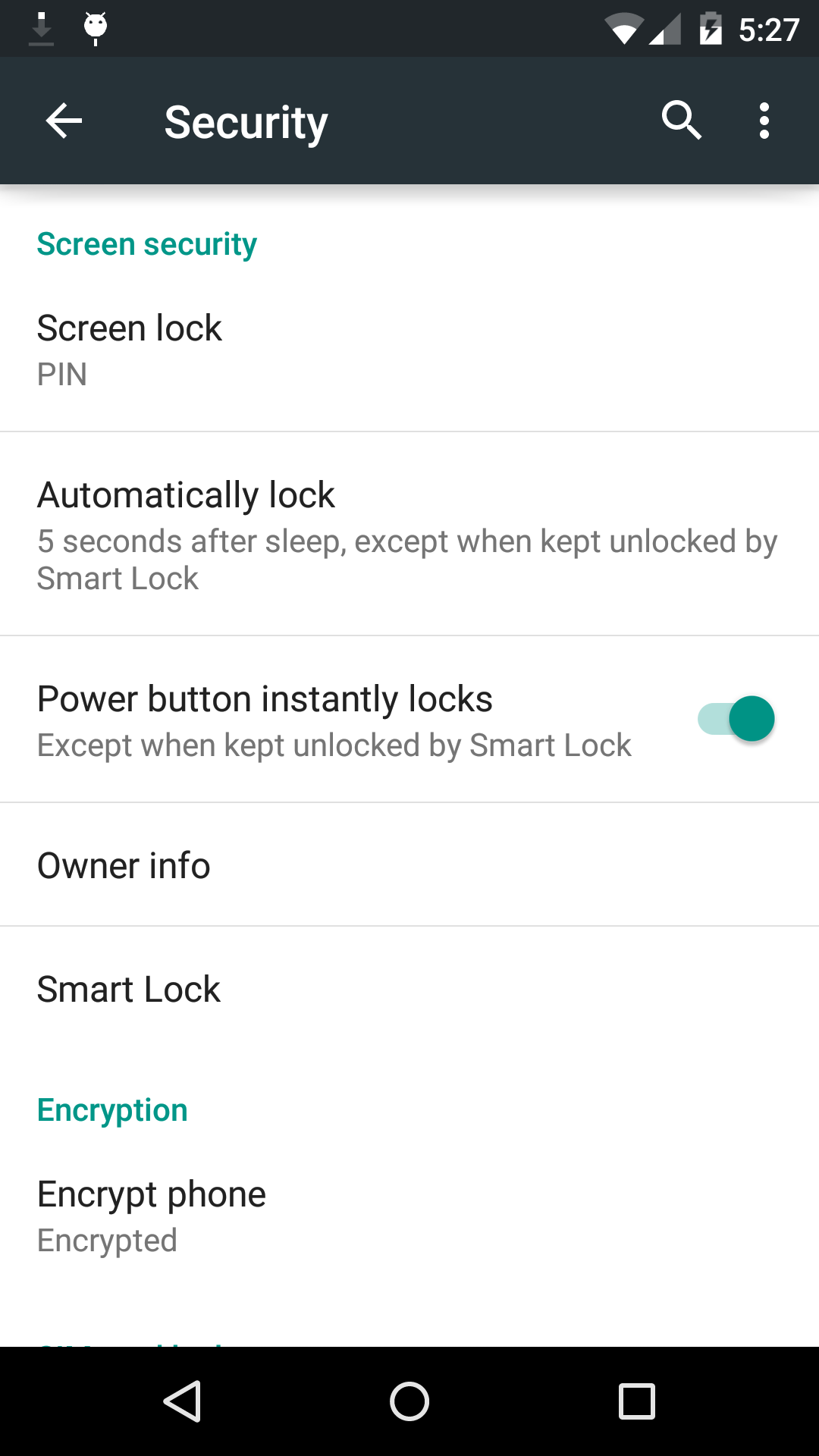
In previous versions of Android, encrypting your phone aka encrypting the /data partition meant that you had to keep using a PIN or password, that would serve both as:
– decryption key to enter during the device boot (that is a component to decrypting the disk decryption key? need confirmation on that)
– lockscreen PIN or password
As you can see in the attached captures, the behavior is entirely different in Android 5.0 Lollipop (here on on Nexus 5).
The first capture show what you see after encrypting your phone after entering a PIN for the screen lock.
Just like before, during boot, the PIN will be asked during boot and to unlock the device.
But now, as you can see in the second capture, you can switch back your screen security to Swipe, or even None.
Then, no password will be asked during boot or in the lock screen.
Yet your data partition is still encrypted.
Question: Where is the disk decryption key stored, and how is it protected?
I look forward to learn that exactly, hopefully a security researcher will take a look at how this new implementation functions, and if it actually provide any security benefit after you revert Screen security to a PIN to Swipe or None.
A question to you, as all my 5.0 devices are already encrypted: can you also now trigger disk encryption without enabling a Screen security first?
Edit:
Yes, you can now indeed encrypt a tablet with Screen lock being set to Swipe or None.
#supercurioBlog #encryption
In Album Android 5.0 Preview encryption
Source post on Google+